NIST CSF 2.0-ALIGNED SECURITY
Govern to Recover. Security built on the full CSF lifecycle.
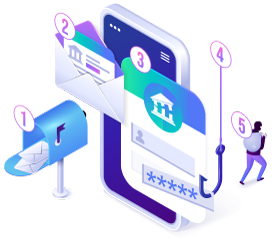
We align your program to the six NIST CSF 2.0 functions - Govern, Identify, Protect, Detect, Respond, and Recover - while applying secure-by-design principles so security is built in, not bolted on.
Book a Risk Review